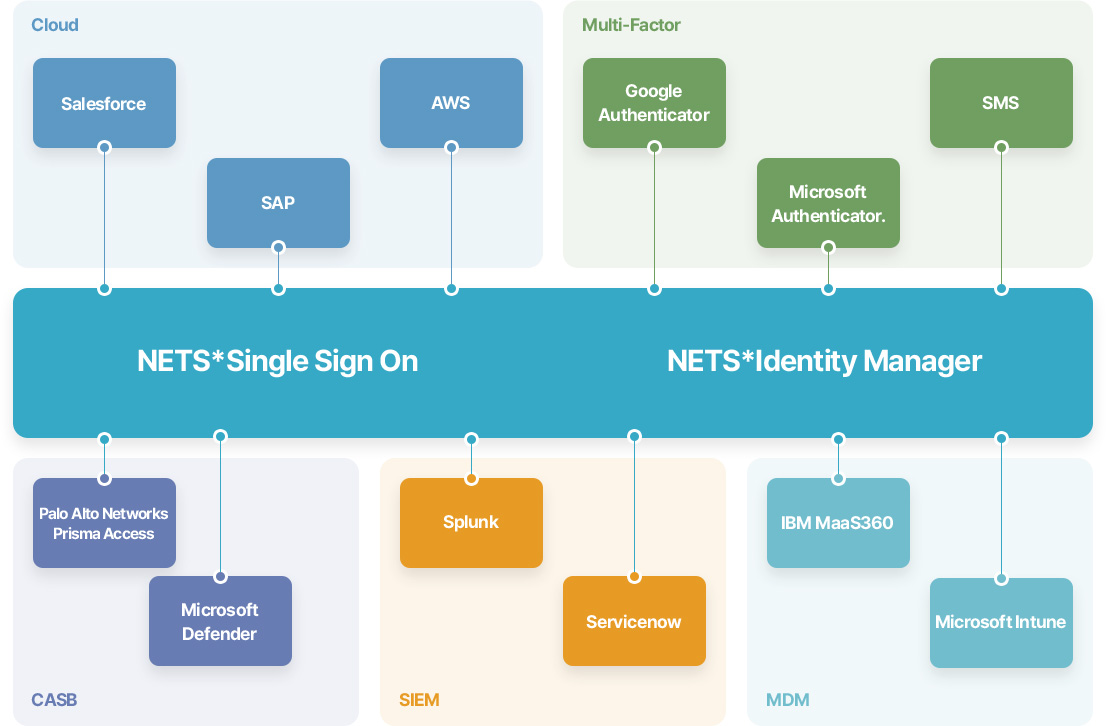
Solution
Zero Trust
Zero Trust
Zero Trust
The importance of account and privilege management in a zero-trust
security model is to continuously validate all access attempts in an
untrusted environment and grant the fewest possible privileges.
The elements that make up Zero Trust can continue to be added as
technology evolves, and SSO and IAM solutions play a key role in how they
work together to effectively secure an organization and protect corporate
assets from internal and external threats.

Expectation Effects
Enhanced
security
Question the trustworthiness of all users and devices and ensure that only verified identities have access to your systems. This prevents not only mistakes or malicious activity from internal employees, but also from external attackers.
Reduce the risk of user account takeover and reduce illegal access or privilege abuse with additional authentication methods.
Regulatory
compliance
Access control and monitoring capabilities help you effectively comply with a wide range of security and privacy regulations. Access to the cloud is monitored and logged in real time, making it easy to provide the data needed in the event of an audit.
Increase IT
asset visibility
All user and device activity is centrally monitored, giving organizations a clear picture of what's happening on their network.
With tighter control over users, devices, and applications, unauthorized access to assets is immediately detected and blocked.
Business
continuity
With real-time monitoring and anomaly detection, you can respond to attacks before they happen or in the early stages to minimize damage.
Deliver security across a wide range of cloud services and on-premises infrastructure, enabling consistent protection across hybrid and multi-cloud environments.
Reduce costs
Centrally manage security policies to reduce the complexity and cost of operating multiple security solutions.
By reducing the likelihood and impact of a breach, you can reduce the cost of incident response and recovery.
Concept Map