Solution
Compliance
Compliance
Identity and Access Management for Compliance
Internal control laws require financial institutions and organizations to
adhere to a set of standards aimed at fostering transparency, reliability,
and compliance with legal regulations.
Identity and access management (IAM) systems play a pivotal role in enabling
these entities to effectively meet the internal control requirements set forth
in these laws.
IAM provides the essential security controls and audit capabilities needed to meet
a diverse range of legal requirements, including those related to privacy,
financial regulations, and external
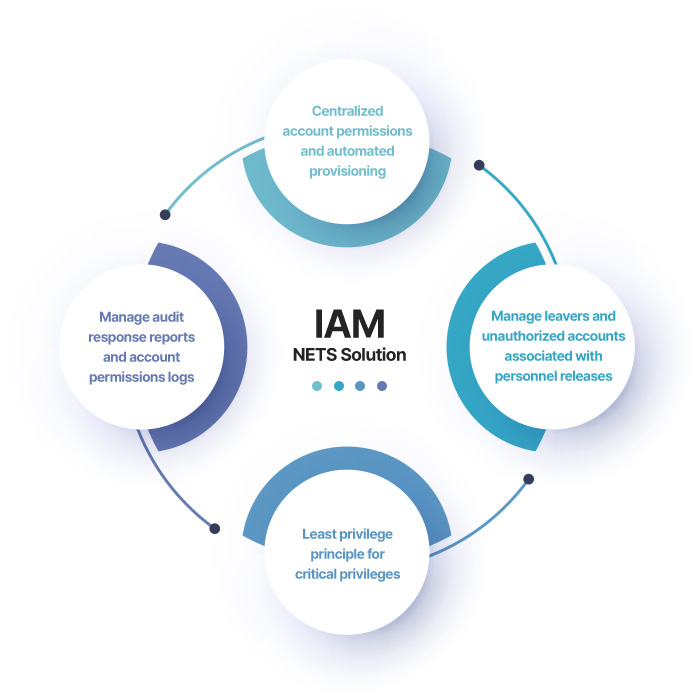
Expectation Effects
Meet regulatory
requirements
This system provides a comprehensive solution for user account and authorisation management, ensuring compliance with a range of regulations, including those related to privacy, internal accounting management and the Information and Communications Network Act (ISMS). It enables organisations to systematically manage the level of information protection, preventing incidents such as hacking and personal information leakage.
Audit response
and recordkeeping
The system automatically saves user activity and access history, creating audit logs. This enables organisations to quickly submit access records in response to regulatory requests or internal audits, and provides clear traceability of access authorisation, revocation, and usage history, making it easier to demonstrate compliance.
Access control and
policy management
Automated provisioning and entitlement management can help you save money by reducing the use of unnecessary accounts or duplicate resources. This reduces the number of unnecessary user accounts and resources in use, enabling more efficient cloud operations. Single Sign-On capabilities reduce user login problems or access issues, which can reduce IT support costs.
Protecting data and
minimizing access
It is essential to apply the principle of least privilege in order to ensure that users are granted only the minimum permissions required to perform their duties. This approach enables the implementation of regulatory-required data protection and access restrictions, which are vital for preventing insider threats and external security breaches.
Rapid response to
regulatory changes
In the event of legislative or industry standard changes, your IAM system can be swiftly updated to align with the new requirements, allowing you the flexibility to respond to regulatory shifts. This mitigates compliance risk and minimises disruption to business operations.
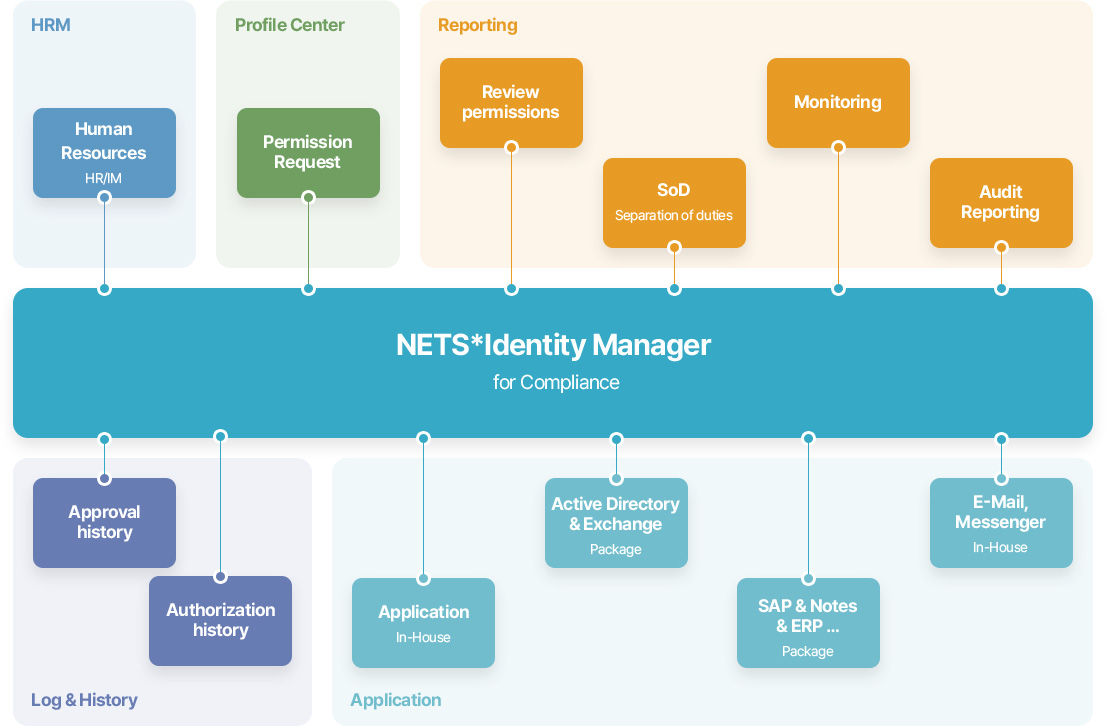
Concept Map